This is an updated version of a post I made on the Now Micro blog last year. The original version of this post can be read Here.
Why is Local Administrator Password Management Needed?
The question of how to deal with users having administrative rights on computers or other network resources is one that has many different answers and has evolved over time. While the scenarios around network and domain administrative access may be more complex, the local administrative rights scenario should be very similar for almost everyone.
A common scenario, in organizations of all sizes, is all workstations sharing the same local administrator account password. The help desk uses this local administrator password when needing to do something on a computer that requires administrative rights. Occasionally this password has been given out to normal users for various reasons.
This scenario has some large security issues.
-
- Help desk users or other network administrators using the local administrator account makes it more difficult to maintain accountability. Actions taken as the local administrator account could have been carried out by anyone with access to the credentials.
- If a normal user is given the local administrator account credentials, they now have local administrator access to every computer with those credentials.
- As more people know the local administrator credentials, the more likely they are to get passed around to other users. Eventually many users that are not supposed to have access to the credentials have them.
- Malware can take advantage of a password being shared across all systems to spread throughout the network.
How to Mitigate These Security Issues
The local administrator account on domain joined devices should rarely, if ever, be used. Ideally, normal users would not have local administrative rights on computers. If a normal user did require local administrative access on a permanent basis, they should have access to a domain account that has been granted local administrative access to their computer. Help desk personnel should have access to domain accounts that are set as local administrators of devices they may need to manage or troubleshoot. Logging in as the local administrator account should be saved for the rare occasion that a computer loses its domain trust relationship and needs to be re-joined to the domain.
Now that the local administrator account is going to rarely be used, it would be nice to be able to change that password, so anyone who previously had known it can no longer use it. This is where Microsoft’s Local Administrator Password Solution (LAPS) comes into play. LAPS is a solution developed by Microsoft to handle the management of the local administrative accounts on domain joined computers. Any device that LAPS is deployed to is able to randomize the local administrator password, store that password in Active Directory, and then change that password on a set schedule.
Install the LAPS Management Utilities
-
- Download the LAPS Installer(s) to a domain joined computer
- Run either the LAPSx64.msi or LAPSx86.msi depending on your computer’s architecture
- At the Welcome screen, click Next
- At the License Agreement screen, accept the EULA and click Next
- At the Feature Installation screen, select to install all the available features, and click Next
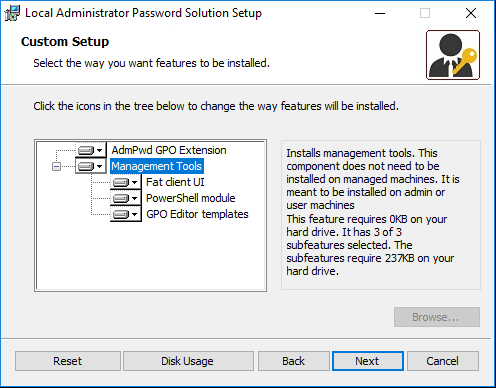
-
- At the Confirmation screen, click Install
- At the Completion screen, click Finish
Extend the Active Directory Schema
LAPS requires an AD schema extension to create the attributes needed to store the administrator password and the password expiration date.
-
- On the computer that the LAPS management utilities are installed on, open a PowerShell prompt with an account that has Schema Admin rights
- Run the command to import the LAPS PowerShell module
Import-Module AdmPwd.PS
-
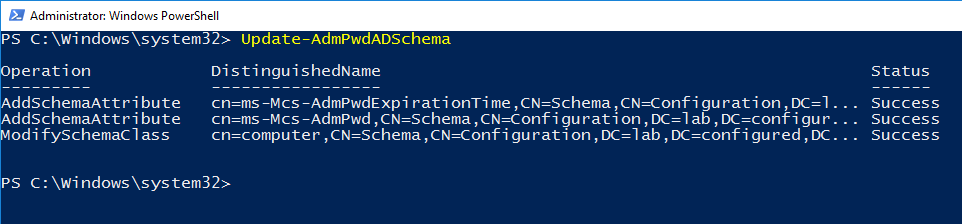
- Run the command to extend the AD Schema
Update-AdmPwdADSchema
-
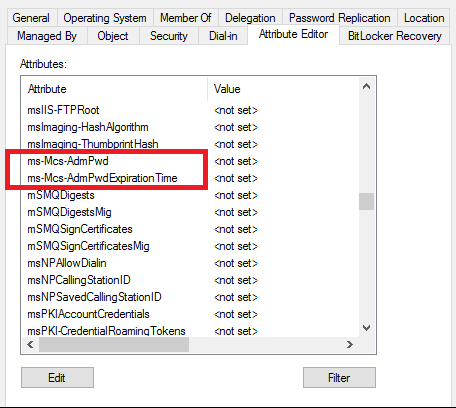
- After extending the schema, there will be two new attributes visible on the properties of the computer objects in AD
- ms-Mcs-AdmPwd – This attribute stores the local administrator password
- ms-Mcs-AdmPwdExpirationTime – This attribute stores the password expiration time
- After extending the schema, there will be two new attributes visible on the properties of the computer objects in AD
Configure Active Directory Computer Permissions
By default, computers will only be able to read the AdmPwd and AdmPwdExpirationTime attributes. For LAPS to work, computers need to be able to write to both attributes. The below steps will grant write permission to both attributes for the SELF account, which will then allow computer objects to update their own password and expiration time attributes.
-
- On the computer that the LAPS management utilities are installed on, open a PowerShell prompt with an account that has Domain Admin rights
- Run the command to import the LAPS PowerShell module
Import-Module AdmPwd.PS
-
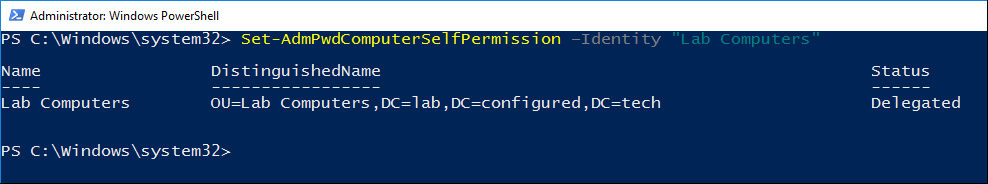
- Run the command to grant write permission to the SELF account. Replace OU Name with the name of the OU that contains computers that will be managed with LAPS. The permissions will apply to any sub OUs of the OU you specify.
Set-AdmPwdComputerSelfPermission -Identity "OU Name"
NOTE: In the examples throughout this article, the common name of the OU is specified. The common name of the OU can be specified if the name is unique, otherwise specify the distinguished name of the OU.
Configure Active Directory User Permissions
By default, only Domain Admins will be able to view and change the password and reset time attributes. These commands will allow you to delegate rights to users or groups to be able to either read or change the attributes.
Delegate rights to an AD user or group to view the password and reset time attributes
-
- On the computer that the LAPS management utilities are installed on, open a PowerShell prompt with an account that has Domain Admin rights
- Run the command to import the LAPS PowerShell module
Import-Module AdmPwd.PS
-
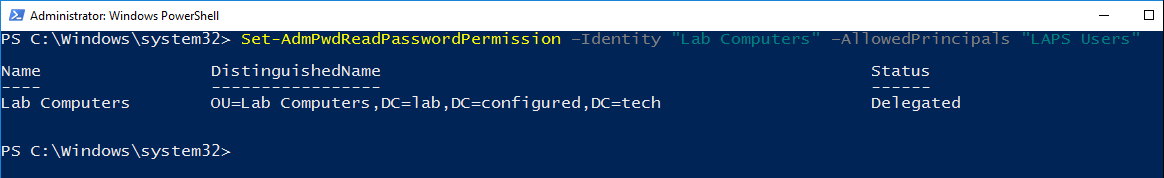
- Run the command to delegate read access to a specific user or group. Replace OU Name with the name of the OU that the user or group will be able to read the attributes for. Replace User or Group Name with the name of the user or group that will be delegated the read permission. Multiple users or groups can be specified in a comma separated list.
Set-AdmPwdReadPasswordPermission –Identity "OU Name" –AllowedPrincipals "User or Group Name"
Delegate rights to an AD user or Group to modify the reset time attribute
-
- On the computer that the LAPS management utilities are installed on, open a PowerShell prompt with an account that has Domain Admin rights
- Run the command to import the LAPS PowerShell module
Import-Module AdmPwd.PS
-
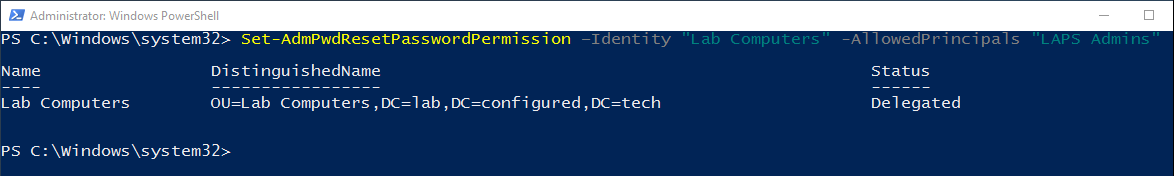
- Run the command to delegate write access to a specific user or group. Replace OU Name with the name of the OU that the user or group will be able to modify the reset time attribute on. Replace User or Group Name with the name of the user or group that will be able to modify the reset password attribute. Multiple users or groups can be specified in a comma separated list.
Set-AdmPwdResetPasswordPermission –Identity "OU Name" -AllowedPrincipals "User or Group Name"
Verify User Permissions
After delegating rights, this command can be run against an OU to determine which users or groups have access to view the password and reset time attributes.
-
- On the computer that the LAPS management utilities are installed on, open a PowerShell prompt with an account that has Domain Admin rights
- Run the command to import the LAPS PowerShell module
Import-Module AdmPwd.PS
-
- Run the command to view the permissions on a specific OU. Replace OU Name with the name of the OU the command will run against.
Find-AdmPwdExtendedRights –Identity "OU Name"
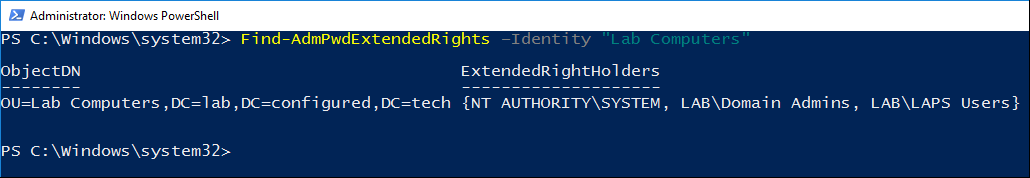
By default, NT AUTHORITY\SYSTEM, and Domain Admins should be listed as extended right holders. Additionally, the group that was delegated read permissions should be listed as an extended right holder.
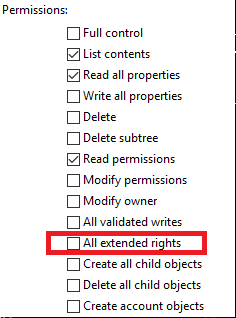
If there are any other users or groups listed under the ExtendedRightHolders property, these could be users or groups that unintentionally have access to view the attributes. This can happen if a user or group was previously delegated rights to this OU and the All extended rights permission was selected.
To make sure any of these extra users or groups cannot view the password or reset time attributes, follow these steps
NOTE: This process removes All extended rights for the selected principal. Make sure the selected principal still has the permissions required to complete any delegated tasks against this OU.
-
- Open Active Directory Users and Computers as an account with Domain Admin rights
- Right click on the OU in question and select Properties
- Click on the Security tab
- Click Advanced
- Select the user or group to modify permissions for
- Click Edit
- Uncheck the All extended rights box
At this point, Active Directory has been configured to support LAPS, computer objects have been given permission to update their password attributes, and the appropriate users have been delegated rights to read and reset the passwords. See Part 2 of this post for instructions on creating the group policy object needed to actually deploy the LAPS functionality to clients.