With all the increased focus on working from home and remote access lately, I figured now would be a good time to share my notes on configuring Always On VPN. This first post will cover the basics of the Always On VPN technology. This guide will be split into multiple parts. Links to each individual post in this series can be found below.
Always On VPN – Certificates and Active Directory
Always On VPN – VPN and NPS Server Configuration
Always On VPN – User Tunnel
Always On VPN – Device Tunnel
Always On VPN – Troubleshooting
I want to preface this series by saying that I am not an expert on this topic. These are my notes based on my experiences working with Always On VPN. I highly recommend reading through the official Microsoft Documentation. Additionally, throughout this series I reference a number of posts by Richard Hicks. If you’re going to be deploying any sort of remote access solution, I recommend bookmarking his website.
How Does Always On VPN Work?
Always On VPN is a solution that allows a client to automatically establish a VPN connection without any user interaction. The technology that makes this possible is the VPNv2 CSP node, which is built into Windows 10. This CSP (configuration service provider) allows the built-in Windows 10 VPN client to be configured using an MDM solution (Intune), or PowerShell.
The server side of a typical Always On VPN deployment requires at least one VPN server and one authentication (RADIUS) server. Additionally, a certificate authority is required to issue certificates to the servers and clients. The certificates will be used to authenticate the VPN connection.
The Windows 10 VPN client can be configured to connect a user authenticated tunnel or a device authenticated tunnel. Both types of tunnels can be connected simultaneously if required.
User Tunnel
The User Tunnel is established when a user logs into a computer. This type of tunnel is ideal for granting access to file shares or applications.
Here is a high-level overview of the connection process for a Always On VPN user tunnel.
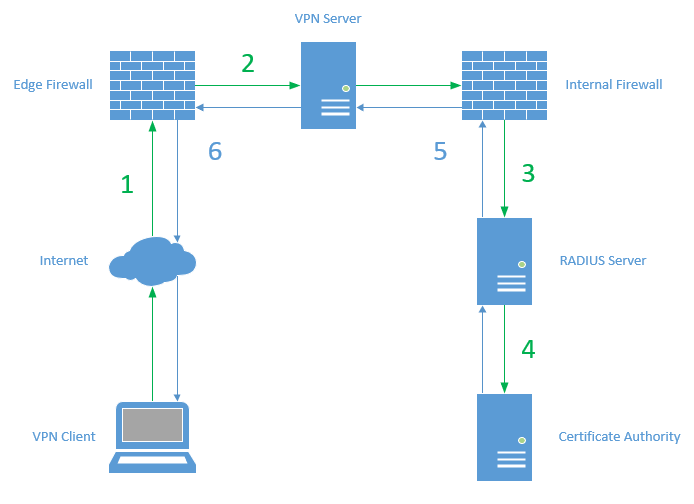
- The VPN client sends a connection request to the external IP address of the VPN server
- The edge firewall passes the connection request to the external interface of the VPN server
- The VPN server passes the connection request to the RADIUS server. The connection request leaves via the internal interface of the VPN server and passes through the internal firewall
- The RADIUS server receives and authenticates the connection request
- The RADIUS server returns an accept or deny response to the VPN server
- The VPN server allows or denies the connection request based on the response from the RADIUS server
Device Tunnel
The Device Tunnel is established as soon as a computer is powered on and connected to the internet. A user does not need to be logged into a computer for a device tunnel to connect. This type of tunnel is ideal for granting access to Active Directory or other management servers like Configuration Manager.
Here is a high-level overview of the connection process for a Always On VPN device tunnel.
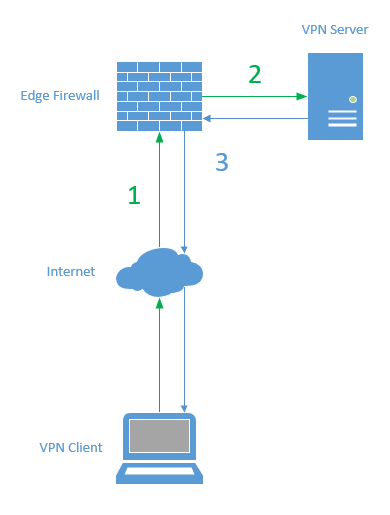
- The VPN client sends a connection request to the external IP address of the VPN server
- The edge firewall passes the connection request to the external interface of the VPN server
- The VPN server validates the computer authentication certificate of the client and allows or denies the connection request
Notice that the device tunnel does not use RADIUS for authentication. The VPN server preforms the authentication. This prevents device tunnels from taking advantage of more advanced Always On VPN features like conditional access and multi-factor authentication. For more guidance on when to utilize device tunnels refer to this post.
VPN Protocols
Always On VPN utilizes familiar VPN infrastructure, which means that it can also utilize familiar VPN protocols. There are two main protocols that make the most sense to use when working with Always On VPN.
IKEv2
Internet Key Exchange version 2 (IKEv2) has good security and good performance. Its ability to automatically re-connect after a short interruption gives it good reliability as well. The primary concern with using IKEv2 is that communication happens on UDP 500 and UDP 4500. This makes it more likely that the connection will be blocked by firewalls.
Note that when using a Always On VPN device tunnel, IKEv2 is the only supported protocol.
SSTP
Secure Socket Tunneling Protocol (SSTP) also has good security, and good performance. The main benefit of using SSTP is that communication happens on TCP 443, so it is very unlikely that it will be blocked anywhere. The downsides to SSTP are that it is not quite as secure as IKEv2, and it does not handle connection interruptions as well.
About this Guide
The goal of this series is to cover the deployment of a basic Always On VPN environment. This guide will assume the reader has existing knowledge of Active Directory Domain Services, Active Directory Certificate Services, DNS, and basic enterprise networking concepts.
This example deployment of Always On VPN will include:
1 VPN server running Windows Server 2019 with the Routing and Remote Access role. This server will be located in a perimeter network and will have 2 network adapters.
1 NPS server running Windows Server 2019 with the Network Policy Server role. This server will be located on in the internal network.
1 VPN client running Windows 10 Enterprise 1909. Both user and device tunnels will be configured.
This deployment will be configured to use IKEv2 for the User Tunnel and Device tunnel.
This guide also assumes Active Directory Domain Services, Active Directory Certificate Services, and Group Policy are installed and functional.
Additional Reading
This guide is for a basic deployment of Always On VPN. There are more advanced features that can be configured but will not be covered here.
Also, remember to check out the full Microsoft Documentation.